Key Management (KMS)
HSM Integration
Learn more about integrating an HSM with Infisical KMS.
Changing the encryption strategy for your instance is an Enterprise-only feature.
This section is intended for users who have obtained an Enterprise license and are on-premise.Please reach out to sales@infisical.com if you have any questions.
Overview
Infisical KMS currently supports two encryption strategies:- Standard Encryption: This is the default encryption strategy used by Infisical KMS. It uses a software-protected encryption key to encrypt KMS keys within your Infisical instance. The root encryption key is defined by setting the
ENCRYPTION_KEYenvironment variable. - Hardware Security Module (HSM): This encryption strategy uses a Hardware Security Module (HSM) to create a root encryption key that is stored on a physical device to encrypt the KMS keys within your instance.
Hardware Security Module (HSM)
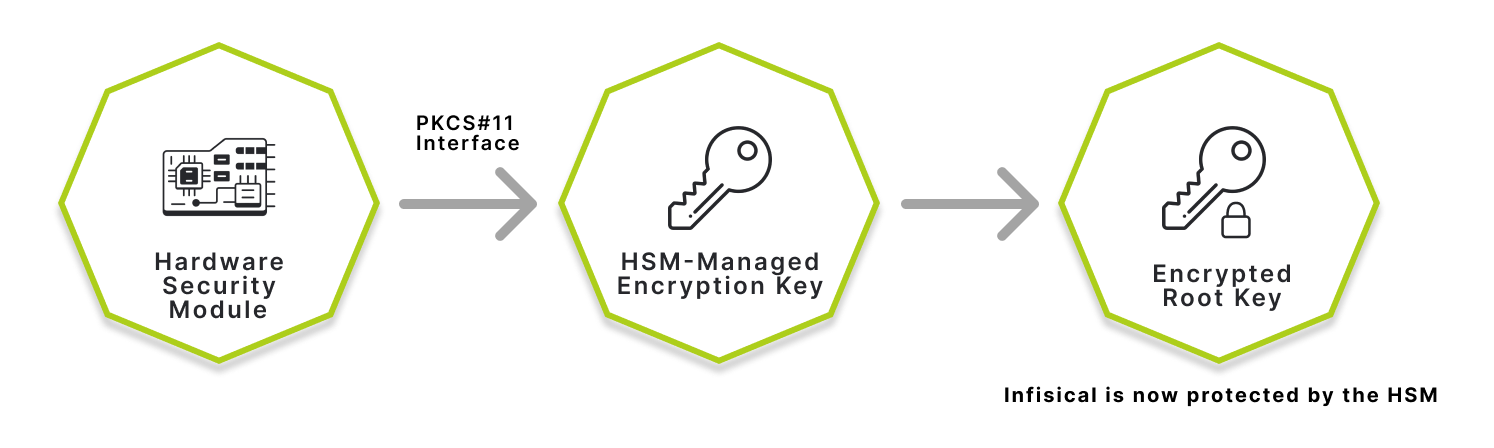 Using a hardware security module comes with the added benefit of having a secure and tamper-proof device to store your encryption keys. This ensures that your data is protected from unauthorized access.
Using a hardware security module comes with the added benefit of having a secure and tamper-proof device to store your encryption keys. This ensures that your data is protected from unauthorized access.
All encryption keys used for cryptographic operations are stored within the HSM. This means that if the HSM is lost or destroyed, you will no longer be able to decrypt your data stored within Infisical. Most providers offer recovery options for HSM devices, which you should consider when setting up an HSM device.
- Root Key Wrapping: The root KMS encryption key that is used to secure your Infisical instance will be encrypted using the HSM device rather than the standard software-protected key.
Caveats
- Performance: Using an HSM device can have a performance impact on your Infisical instance. This is due to the additional latency introduced by the HSM device. This is however only noticeable when your instance(s) start up or when the encryption strategy is changed.
- Key Recovery: If the HSM device is lost or destroyed, you will no longer be able to decrypt your data stored within Infisical. Most HSM providers offer recovery options, which you should consider when setting up an HSM device.
Requirements
- An Infisical instance with a version number that is equal to or greater than
v0.91.0. - If you are using Docker, your instance must be using the
infisical/infisical-fipsimage. - An HSM device from a provider such as Thales Luna HSM, AWS CloudHSM, Fortanix HSM, or others.
Setup Instructions
1
Setting up an HSM Device
To set up HSM encryption, you need to configure an HSM provider and HSM key. The HSM provider is used to connect to the HSM device, and the HSM key is used to encrypt Infisical’s KMS keys. We recommend using a Cloud HSM provider such as Thales Luna HSM, AWS CloudHSM, or Fortanix HSM.You need to follow the instructions provided by the HSM provider to set up the HSM device. Once the HSM device is set up, the HSM device can be used within Infisical.After setting up the HSM from your provider, you will have a set of files that you can use to access the HSM. These files need to be present on the machine where Infisical is running.
If you are using containers, you will need to mount the folder where these files are stored as a volume in the container.The setup process for an HSM device varies depending on the provider. We have created guides for Thales Luna Cloud HSM and Fortanix HSM, which you can find below.
2
Configure HSM on Infisical
Are you using Docker or Kubernetes for your deployment? If you are using Docker or Kubernetes, please follow the instructions in the Using HSM’s in your Deployment section.
HSM_LIB_PATH: The path to the PKCS#11 library provided by the HSM provider. This usually comes in the form of a.sofor Linux and MacOS, or a.dllfile for Windows. For Docker, you need to mount the library path as a volume. Further instructions can be found below. If you are using Docker, make sure to set the HSM_LIB_PATH environment variable to the path where the library is mounted in the container.HSM_PIN: The PKCS#11 PIN to use for authentication with the HSM device.HSM_SLOT: The slot number to use for the HSM device. This is typically between0and5for most HSM devices.HSM_KEY_LABEL: The label of the key to use for encryption. Please note that if no key is found with the provided label, the HSM will create a new key with the provided label.
3
Restart Instance
After setting up the HSM, you need to restart the Infisical instance for the changes to take effect.
4
Navigate to the Server Admin Console
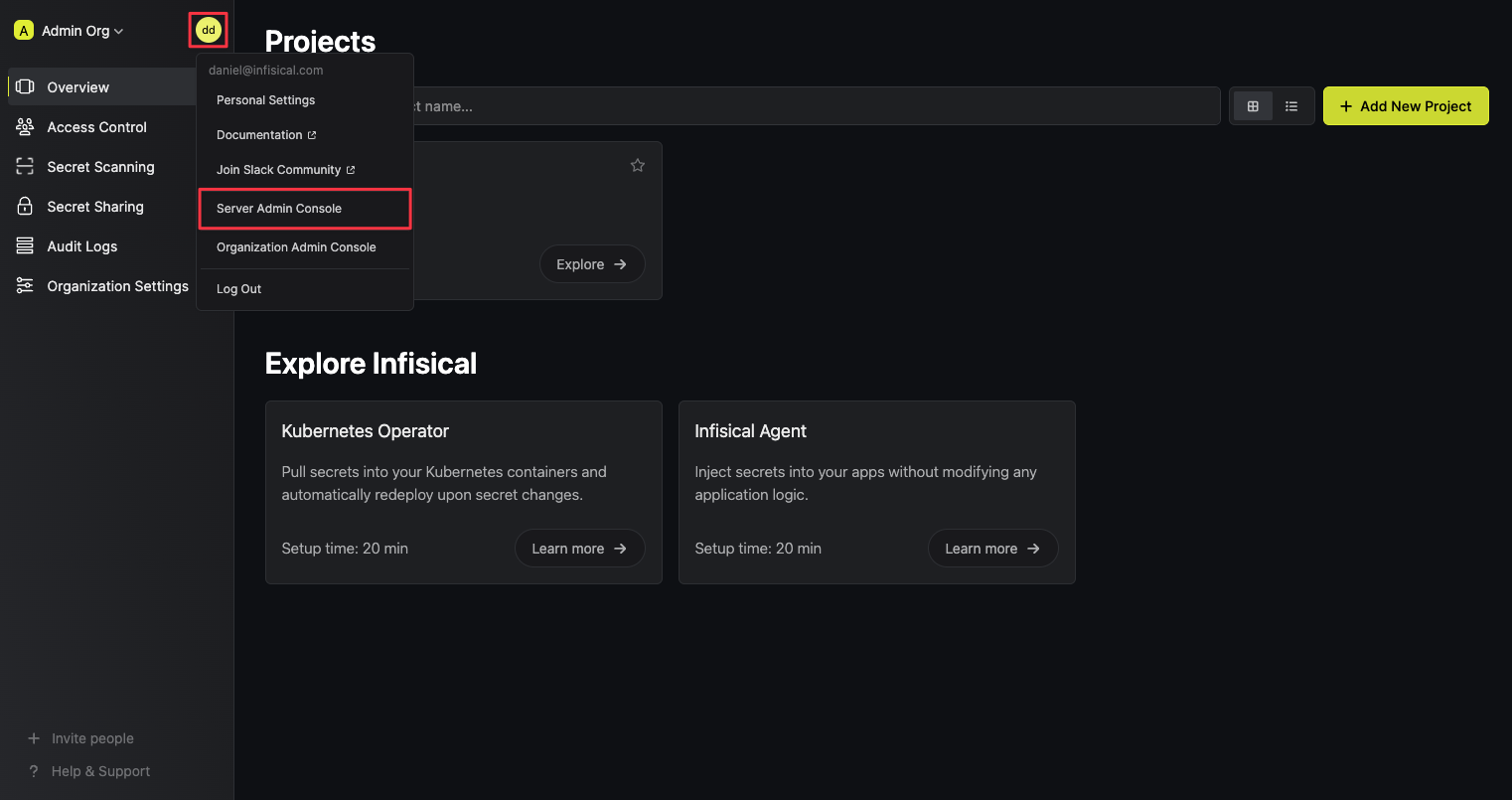
5
Update the KMS Encryption Strategy to HSM
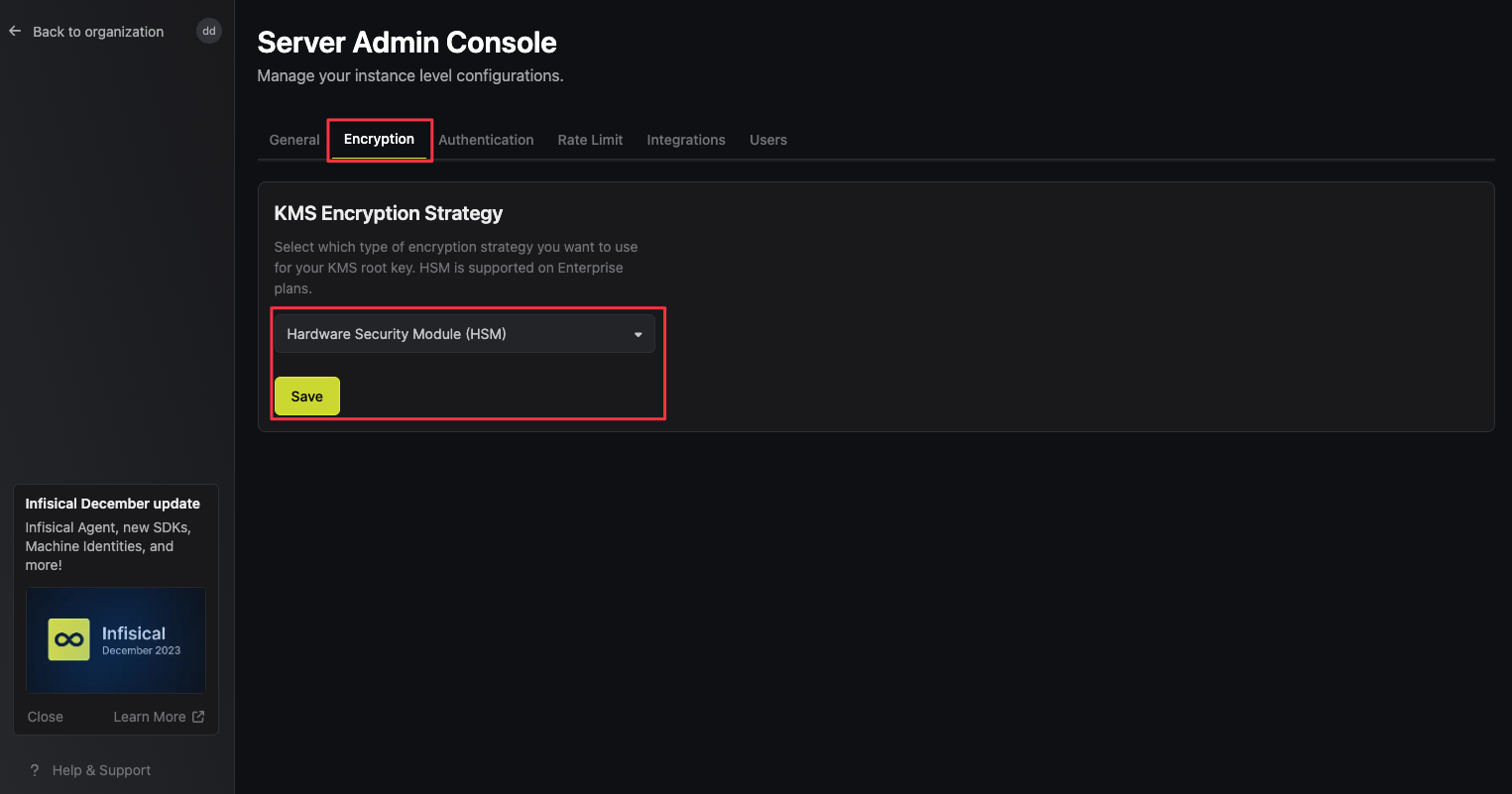 Once you press the ‘Save’ button, your Infisical instance will immediately switch to the HSM encryption strategy. This will re-encrypt your KMS key with keys from the HSM device.
Once you press the ‘Save’ button, your Infisical instance will immediately switch to the HSM encryption strategy. This will re-encrypt your KMS key with keys from the HSM device.6
Verify Encryption Strategy
To verify that the HSM was correctly configured, you can try creating a new secret in one of your projects. If the secret is created successfully, the HSM is now being used for encryption.
Using HSMs In Your Deployment
When using Docker, you need to mount the path containing the HSM client files. This section covers how to configure your Infisical instance to use an HSM with Docker.After following these steps, your Docker setup will be ready to use HSM encryption.
1
Create HSM client folder
When using Docker, you are able to set your HSM library path to any location on your machine. In this example, we are going to be using After setting up your Luna Cloud HSM client, you should have a set of files, referred to as the HSM client. You don’t need all the files, but for simplicity we recommend copying all the files from the client.A folder structure of a client folder will often look like this:The most important parts of the client folder is the
/etc/luna-docker.Chrystoki.conf file, and the libs, plugins, and jsp folders. You need to copy these files to the folder you created in the first step.2
Update Chrystoki.conf
The Save the file after updating the paths.
Chrystoki.conf file is used to configure the HSM client. You need to update the Chrystoki.conf file to point to the correct file paths.In this example, we will be mounting the /etc/luna-docker folder to the Docker container under a different path. The path we will use in this example is /usr/safenet/lunaclient. This means /etc/luna-docker will be mounted to /usr/safenet/lunaclient in the Docker container.An example config file will look like this:3
Run Docker
Running Docker with HSM encryption requires setting the HSM-related environment variables as mentioned previously in the HSM setup instructions. You can set these environment variables in your Docker run command.We are setting the environment variables for Docker via the command line in this example, but you can also pass in a We recommend reading further about using Infisical with Docker.
.env file to set these environment variables.If no key is found with the provided key label, the HSM will create a new key with the provided label.
Infisical depends on an AES and HMAC key to be present in the HSM. If these keys are not present, Infisical will create them. The AES key label will be the value of the
HSM_KEY_LABEL environment variable, and the HMAC key label will be the value of the HSM_KEY_LABEL environment variable with the suffix _HMAC.Disabling HSM Encryption
To disable HSM encryption, navigate to Infisical’s Server Admin Console and set the KMS encryption strategy toSoftware-based Encryption. This will revert the encryption strategy back to the default software-based encryption.
In order to disable HSM encryption, the Infisical instance must be able to access the HSM device. If the HSM device is no longer accessible, you will not be able to disable HSM encryption.

